Instructions
Q&A (0)
Notes (0)
Resources (0)

Saving Progress...
Resources
There are no resources for this lesson.
Notes can be saved and accessed anywhere in the course. They also double as bookmarks so you can quickly review important lesson material.
In this lecture, I am going to talk to you about Windows Trusts and help you understand what they are and how they work.

So, before we get started, let’s quickly talk about what a Windows Domain is.Now, as you know, a Windows Domain is like a collection of resources. User accounts, computers, printers, etc. So if I have my domain instructorpaul.com or itflee.com, then I am generally going to have User Accounts and Computers that are associated with that domain. It can also be printers and other types of resources.

Let’s talk about, What Is A Trust?
Now, a Trust allows users in one domain to access resources in another Domain. That is at the most basic level.There are three main components that define Trust. There’s the Type of the Trust, there’s Transitivity, and there’s the Direction of the Trust.

So, let’s talk more about the Type of Trusts.
Now, the first type that we have is the Parent-Child type. This is the trust that is automatically created if you add a Subdomain.So, if I have Domain A and I create Domain D, and it's a Subdomain to Domain A, then there will be an automatic two-way Transitive Trust that will be created between Domain A and Domain D, and this would be a Parent-Child Trust.
So, if I have instructorpaul.com and I add a Subdomain called courses.instructorpaul.com that would be a two-way Transitive Trust automatically, created between instructorpaul.com and courses.instructorpaul.com.

Next, we have a Tree Root Trust which is also automatically created when a new Tree Root Domain is added to an existing Forest. These Trusts are two-way Transitive Trusts as the Parent-Child.
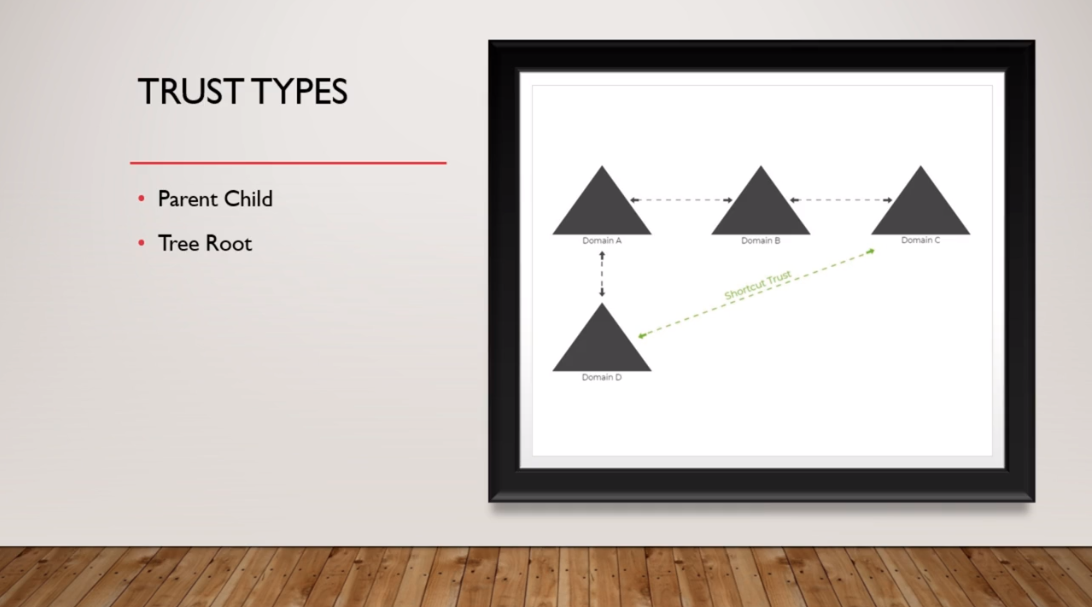
Next, we have a Shortcut Trust that is manually created and only exists within a specific Forest. They are created to optimize the authentication process and these Trusts are Transitive and they can be either one-way or two-way.So, here on this picture we can see we have Domain A, Domain B, and Domain C. Now, we are going to talk more about Transitivity later on, but let’s say that all these domains trust each other.
Let’s say that Domain D needs to authenticate a user from Domain C. Well, it would have to go to Domain A and then over to Domain B and then over to Domain C. You could create a Shortcut Trust that would allow this Domain D to skip all these domains and go over directly to Domain C. That’s the purpose of a Shortcut Trust. Literally, it is just making the authentication process faster.

Now, a Forest Trust is just it sounds. It allows you to establish a one-way or two-way trust between two Active Directory Forests.As a side note, a Forest if you don’t already know is a collection of Trees and a Tree is just a collection of Domains, just like what we have in the picture.

Next, we can have an External Trust. These are non-transitive one-way trusts that are used to access resources in the NT4.0 domain or a domain in another forest that does not have a forest trust established. So, you can create these External trusts between two different domains that aren’t trusting, or the forest doesn't trust each other.

Now, finally, you can have a Realm Trust. These are used to access resources between a Non-Windows Kerberos version 5 Realm and an Active Directory Domain.
Kerberos is a network authentication protocol. You can learn more about Kerberos authentication if you are interested in the following link.Reference: Kerberos Realm definition: https://docs.oracle.com/cd/E36784_01/html/E37126/kintro-56.html

Now, let’s talk about Transivity.
First, there are two things you need to learn about transivity, you have Transitive Trust and Non-transitive Trust.A Transitive Trust means that the trust can be extended beyond the two domains for which the domain or the trust was established. For example, Domain A establishes trust with Domain B, and that is a transitive trust, and Domain B has also a trust established with Domain C, then users in Domain C could be used to access resources in Domain A if the appropriate permissions were configured. So if Domain A trusts Domain B and Domain B trusts Domain C then that means Domain A also trusts Domain C.
So, when you set up a Transitive Trust you are not only saying Domain A is going to transitively trust Domain B, we are also going to trust all the domains that Domain B trusts.Now, on the other hand, if I establish non-transitive trust between Domain A and Domain B it wouldn’t matter what domains that Domain B trust, my non-transitive trust allows users in Domain B to access resources in Domain A. So, being non-transitive is a more restricted way to establish trust between the domain.

Now, let’s talk about Trust Direction and Flow.
You can have a One-way Trust, which on the picture on the right-hand side of the screen we have Domain A which has established one-way trust with Domain B. That means users in Domain B could be used to access resources in Domain A, but users in Domain A could not be used to access resources in Domain B.If we have a Two-way Trust, that means users in either Domain can be used in the other Domain to access resources. So, Domain A could be used in Domain B could be used in Domain A.

Now, here are all the Possible Trust Combinations that we’ve talked about.
On the left-hand side, we have the Trust Types which is what we’ve talked about earlier, then we have the Characteristics, Direction, Authentication Mechanisms, and some notes.

OK, that is all that I have for you in this lecture.
Reference: Kerberos Realm definition: https://docs.oracle.com/cd/E36784_01/html/E37126/kintro-56.html


